Industry
Solution
Highlights
- Information Technology (IT) and Operational Technology (OT) developed as two divergent threads of digitization due to their different focus areas— automation of information and automation of equipment and processes, respectively.
- But innovative technologies such as AI, IoT, cloud, are driving the IT-OT convergence that is benefitting asset-heavy companies, especially in utilities and energy sectors.
- For instance, with the advent of innovations like digital twins, utility companies are looking to go beyond traditional digitization to explore innovative business ideas.
On this page
Digital synergy
While digital transformation is the buzzword across all major industries, the traditional asset-heavy critical infrastructure sector (CIS) companies—especially in the utilities and energy domains—are stuck in the middle between the demands of business, technology, and security.
The utility business, for instance, is undergoing serious industry transformation. The industry faces impacts of the 3Ds—decarbonization, decentralization, and digitalization.
Nimble power generators are threatening large power plants, grids are getting decentralized, traditional strengths of “integrated value-chains” are becoming “less integrated ecosystem networks”, one-way energy flow is becoming bi-directional with solar rooftops and electric vehicles making consumers into prosumers, a significant increase in electrification of public and private transport from trucks to trains to vans and e-scooters are increasing load and volatility on the grid while increasing sustainability demands and customers demanding more intimacy, flexibility, and transparency are forcing business leaders to think out-of-the-box.
The CIO of a large Asian integrated power utility company says, “We want to go beyond just selling kilowatts to move into e-commerce, facilities management, energy management services...” He adds, “… And we need to change our mindsets and strategies. We must be more OPEX than CAPEX driven in our investment strategy, free up our resources from mundane, repetitive tasks, get our people to manage by exceptions, focus them to shape new business initiatives, be agile, take a pragmatic and holistic look at risks and be digitally upskilled…”.
Driving digitization
Digital technology has been at the core of power utilities and has driven digitization for a long time.
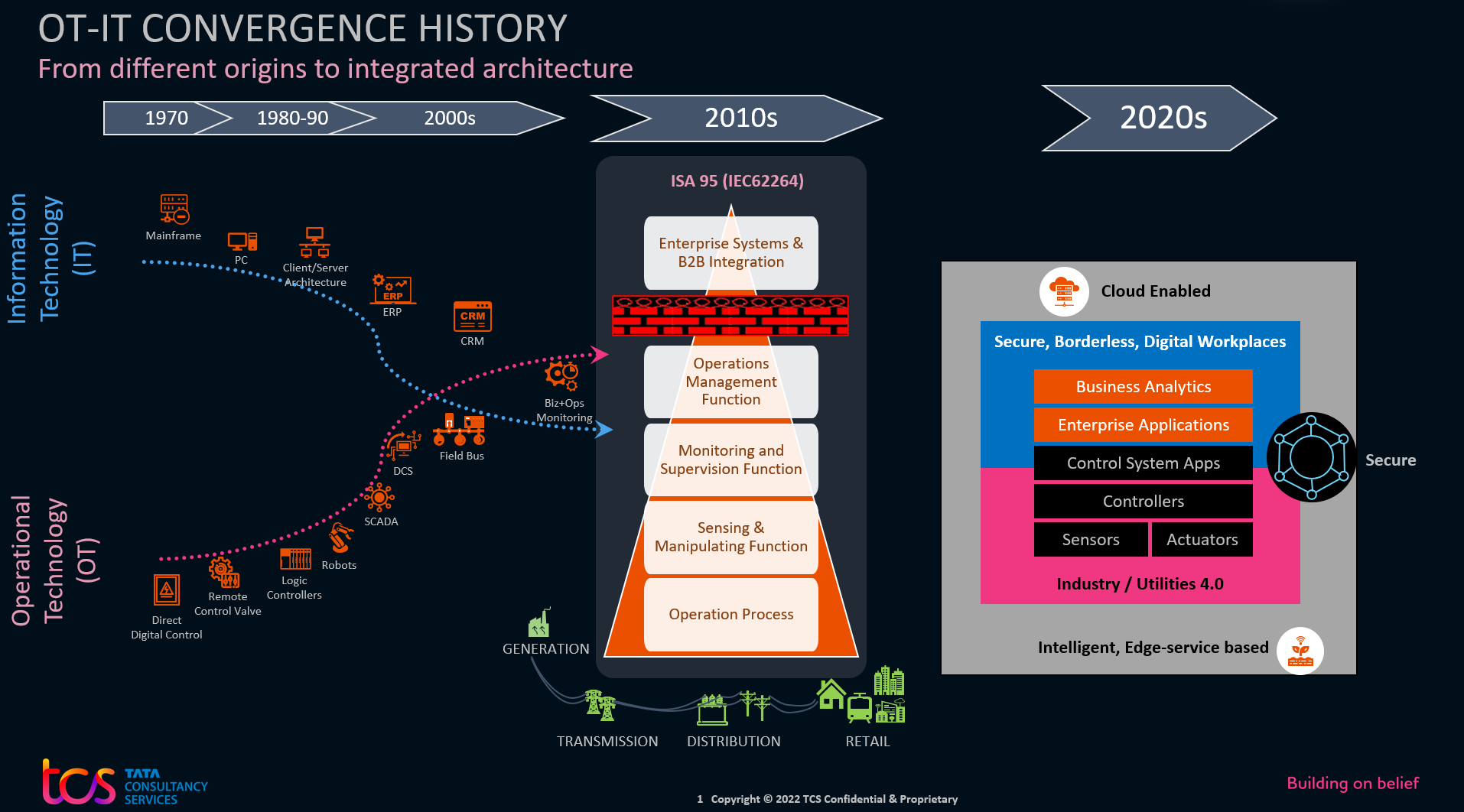
Information Technology (IT) focuses on the automation of information for business. Front-office and back-office functions have evolved rapidly and have come a long way from mainframes to PCs, to client servers, and now to cloud architectures. Confidentiality, integrity, and availability are the core tenets of IT. CIOs have been running IT, which is in charge of fast-depreciating assets such as laptops, smartphones, servers, printers, and other office equipment.
Operational Technology (OT), on the other hand, came with the intent of automating plant equipment and processes. It started off well with the Direct Digital Control Valves, gradually evolving into logical controllers, SCADA (Supervisory Control and Data Acquisition), and DCS (Distributed Control Systems), with fieldbus network systems trying to integrate process control equipment and assets. Safety and reliability are the core tenets of OT. Chief Operating Officers (COOs) with plant managers have been responsible for it. They are used to working on long-depreciating assets—such as turbines, transformers, boilers, and others that work tirelessly over 20-30 or even over 50 years.
The division between OT and IT became deeper with different standards (e.g., ISO27001 for IT and IEC62443 for OT), vendors (e.g., ERP/CRM vendors like SAP, Oracle, Salesforce for IT and OEMs like Siemens, GE for OT), and mistrust (OT fearing an IT take-over). Adding to the chasm are security folks, acting as blockers — stopping any two-way communication between OT and IT.
Due to its origins and tenets, digitization has been divergent. The traditional digitization mindset is to apply new technologies to old processes. Data is collected and historized for conventional reporting. Data is rarely used to explore new businesses and as a lifeblood of innovation to transform operating models.
Innovation to the rescue
Innovations, primarily in the technology space, are forcing utilities to integrate OT and IT by reducing costs and simplifying complexities.
Greater chip densities and higher disk and network capacities provide economies of scale. Real-time publish/subscribe messaging middle-wares have cropped up that facilitate easy exchange of synchronized and asynchronous communications. Web-services-oriented architecture over Gigabit backbones and wireless ethernet radios over 5G provide more secure communications between control centers and remote field devices. Broadband networks today support Advanced Metering Infrastructure (AMI).
OT systems like SCADA, Outage Management Systems (OMS), and Distribution Management Systems (DMS) have become more acceptable to IT and are running today on Windows/Linux-based IP-enabled networks. IEC and IEEE standards are maturing and getting more industry specific. For instance, IEC 61968 covers a Common Information Model (CIM) for distributed operations through AMI. Analog 4-20 mA, 0-10V and discrete signals have now merged into the IO-Link protocol. IEC62264, also called ISA95, dispositions OT and IT into five levels with De-militarized Zones (DMZ) for robust security. Modbus, Profibus, and DeviceNET protocols can now be routed via standard and free OPC UA with MQTT. IT standards and protocols such as FTP, SQL/ODBC, and HTTP/REST are readily available for OT, and OEM vendors are actively touting them.
Artificial Intelligence (AI) and Machine Learning (ML), IoT, big data operational analytics over cloud, edge and fog computing are pushing intelligence to the field, right to the sensor level, and bringing the power to transform existing business models by unlocking the potential of energy-as-a-service solution and driving power utilities to be “smart” energy companies.
Smart mobile devices are transforming remote ways of working field. Field crews now have more access to near real-time data and optimization, enabling them to have better situational awareness, and undertake design switching decisions, inspections, on-demand equipment operating history, damage assessments, and inventory tracking, thereby having the potential to be smart workers.
Digital Twins allow power utilities to build virtual replicas of physical objects and assets. Engineers and operators can assess environmental factors, simulate scenarios, and identify how adverse events impact quality and productivity. Augmented Reality (AR) connected systems allow overseeing installations meshed with enhanced training simulations and can provide on-demand digital guides for complex repairs. Edge computing with Generative AI (like ChatGPT) is poised to converse with IoT (Internet of Things) and IIoT (Industrial Internet of Things) and get insights from consolidated data on a real-time basis rather than waiting for batch conversion of machine-generated data into actionable insights.
Figure 1: Mapping the IT-OT convergence journey over the decades.
With the advent of these innovations, utilities are looking to go beyond traditional digitization. Instead of applying new technologies to old processes they seek to explore new business and operating models with technology to ignite growth and profitability by adding value to their loyal customer base.
Data: The lifeblood unblocked
Technological innovations give rise to an explosion of data.
OT-IT convergence breaks siloed data ownership and allows a seamless and secure flow of data. This data flow increases in value from the field sensors and is transformed into knowledge and insights for the board room.
OT-IT convergence use cases unblock quality data, which become a strategic enterprise asset that leads to new capabilities and efficiencies drawn from insights, accelerating growth, innovation, and, thereby, monetization and financial performance.
As with every other strategic asset, data from the convergence needs to be carefully governed. It needs to be unearthed, cleansed, standardized, catalogued, stored, processed, tracked, and analyzed with clear ownership and consensus amongst the people who use them. There are multiple benefits to this, including acceleration in digital transformation, reduced cost of carrying data, empowered individuals, greater trust in data equates to greater trust in business as a going concern, proactive decision making.
Cyber resilience
The effect of cyberattacks on an OT system has far higher and more negative consequences than on an IT system.
Cyber-attackers could use less secure third-party connections on these OT devices. It could lead to outages, leakages, shutdowns, or even explosions.
Due to the nature and long history of its business, CISs typically have many distributed legacy systems, some of them more than 30 years old, with vulnerabilities and limited security controls. Limited cyber resilience of equipment supplied by OEMs (e.g., those providing valves, sensors, or actuators) in remote substations before cybersecurity hardening carries high risks. Power utilities and oil and gas, being continuous processes, may run for about three years before a planned maintenance activity, which restricts OT teams to patch devices that need to be always on.
Segmentation and securing of OT networks with proper De-Militarized Zones (DMZs), proper implementation of security controls with secure network reference architecture with strictly configured security controls, constant asset threat detection with clear cybersecurity posture, with clear ownership, roles and responsibilities between OT and IT teams to defend plant assets are a must. Cybersecurity leaders should work as “partner enablers” with OT and IT on a co-owned risk framework tackling residual risk with appropriate security controls, policies, and procedures.
The skill set challenge
Lack of skills and ownership, especially on the OT side, rank as the top challenges against OT-IT Convergence.
Though programming logic is the underlying skill thread between OT and IT systems, OT requires different skill sets and competencies. OT personnel focus on engineering, maintenance, and operations with a focus on reliability. OT roles require knowledge of systems and cybersecurity, which is difficult to find. Cross-pollination of personnel between OT and IT, joint program ownership for integrating projects — for instance, IoT devices with edge computing and participation in simulated hackathons would raise awareness and improve skill sets of personnel.